[ cross-posted from Zenpundit ]
We’ve been having an intriguing discussion recently in the comments on Zenpundit about mapping / modeling complex situations in a way that leaves us humans more liable to come to nuanced understandings and less liable to unintended consequences, and one point that keeps on cropping up is the need to pare down the number of nodes in our mapping without losing sight of the subtleties…
I was thus delighted to find, as I was doing my morning trawl of usual and unusual news sources, that Glenn Beck had come out with his estimate of how many Muslim terrorists there are in the world (10% of the global Muslim population, ie 157 million), Fareed Zakaria had refuted him — and there was even a helpful Silobreaker network diagram to show me how the relevant nodes under discussion fit together:
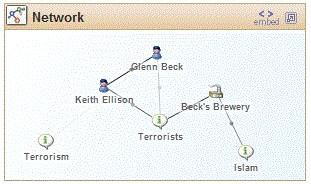
I was delighted to see that (Mormon) Glenn Beck is more closely associated with (Muslim) Rep. Keith Ellison than he is with terrorists, and sorry to note that Beck’s Brewery and Islam are somehow linked… But naturally, once I had seen this much I wanted to drill down even deeper — so I entered the appropriate keywords at Silobreaker and found this:
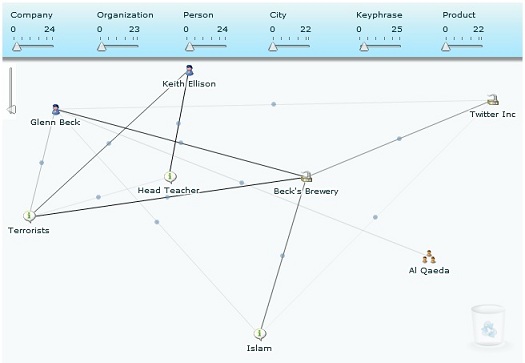
You’ll see that Beck’s link with Al Qaeda is, thankfully, a weak one. And I think you’ll agree with me that even shifting from a six node to an eight node graph considerably ups the sophistication of analysis required to fully comprehend the issues portrayed.
*
In any case, I thought it might be appropriate to post Silobuster’s more detailed map of the current situation with WikiLeaks here:
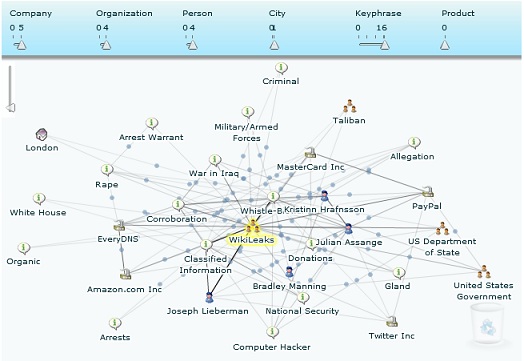
All becomes clear, eh?
I particularly like the node labeled “Gland” (it’s almost hidden but not quite, you’ll find it lower right, between PayPal and Twitter)– that might be the one I’d zero in on to get a fuller appreciation of the complexities of the situation.
And for the record, this post is an example of British “humor” — or as we prefer to call it, “dry wit”.
This is starting to remind me a little bit of Robert Anton Wilson. Even the squirrels in the trees are in on the conspiracy. What conspiracy? You know, the conspiracy.
Yup.
There was even Xeni Jardin’s allegation (now withdrawn) that the CIA had set up its own “honeypot” WikiLeaks server — and there appear to have been faked WikiLeaks diplomatic cables circulating in parts of the Pakistani press…
Cyberwars and rumors of cyberwars…
Indeed, it seems there’s plenty of room in conspiracy space for WikiLeaks: